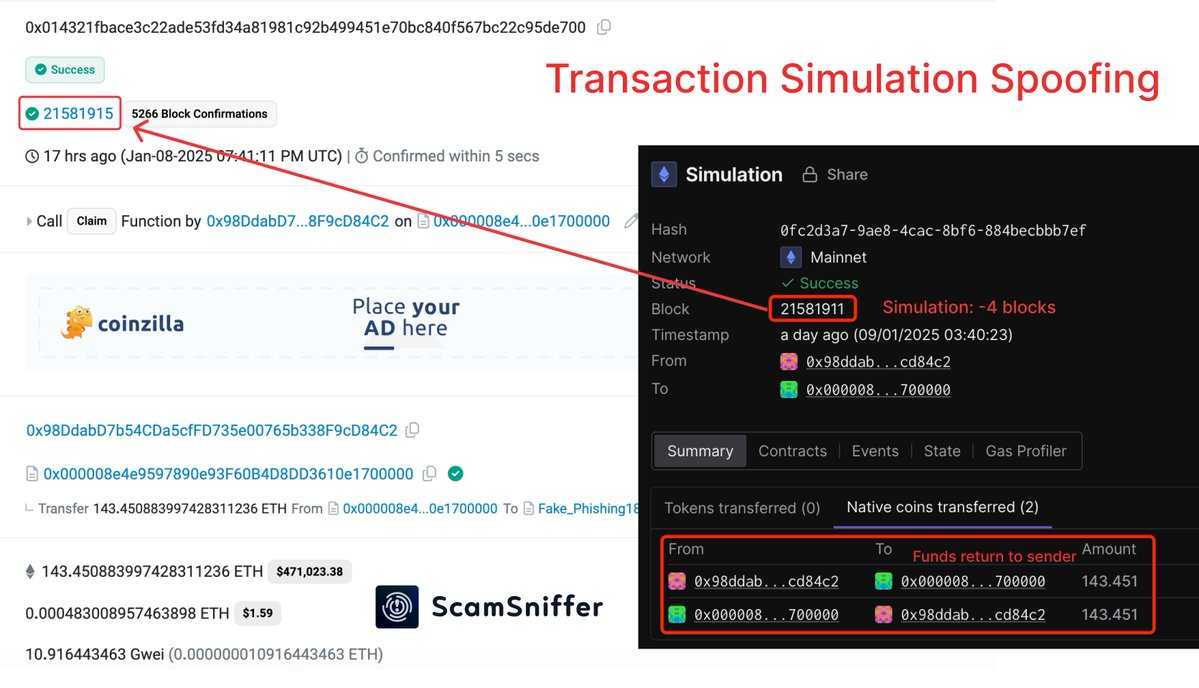
In a recent cybersecurity incident, a victim lost 143.45 ETH, valued at approximately $460,895, one day ago due to a sophisticated phishing attack known as transaction simulation spoofing. This attack exploited the delay between transaction simulation in modern Web3 wallets and its actual execution, allowing attackers to manipulate on-chain states immediately after transaction submission.
Details:
Scam Sniffer | Web3 Anti-Scam (
@realScamSniffer
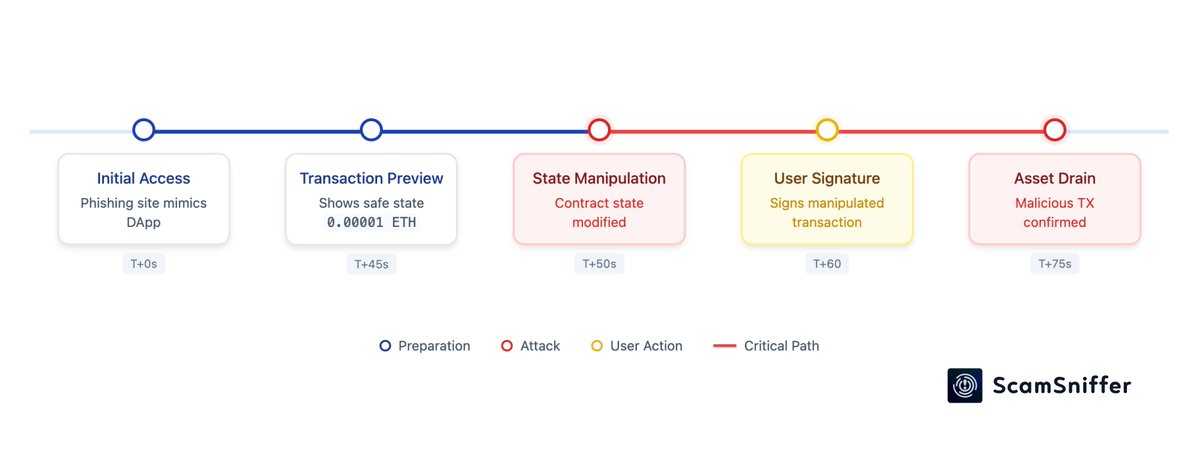
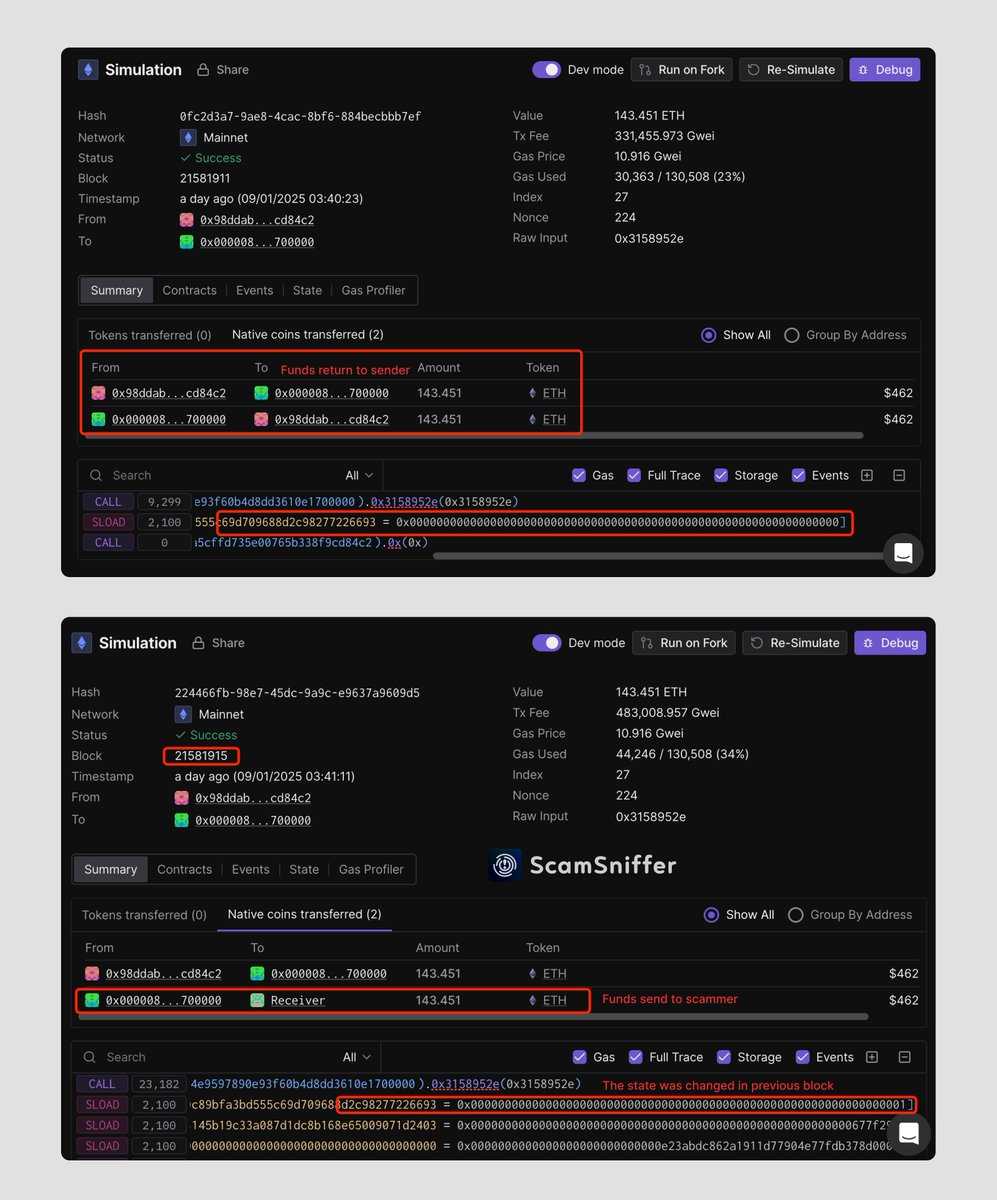
) posted a thread on X, detailing how these attacks operate. Attackers create phishing sites that trick victims into initiating a fake “Claim” ETH transfer. The wallet simulates receiving a tiny amount of ETH (0.000…0001 ETH), but in reality, the transaction modifies the contract state in the backend, leading to the wallet being completely drained.
According to Scam Sniffer’s recommendations, users should double-check transaction details, verify contract interactions, be cautious of “free claim” offers, and only use trusted decentralized applications (dApps) to avoid such attacks. To enhance wallet security, suggestions include dynamic refresh based on block time, forcing a simulation refresh before signing, showing simulation timestamps, integrating phishing contract blocklists, and alerting for outdated simulation results.
This type of attack represents an advanced evolution in phishing strategies, underlining the necessity for vigilance and verification through multiple sources when dealing with blockchain transactions.
A victim recently lost 143.45 ETH, valued at approximately $460,895, due to a sophisticated phishing attack known as transaction simulation spoofing.
This attack exploits the delay between the simulation of a transaction in modern Web3 wallets and its actual execution, allowing attackers to manipulate on-chain states post-submission.
The phishing site involved initiated a fake “Claim” ETH transfer, leading the victim’s wallet to simulate receiving a minuscule amount of ETH before the actual transaction drained the wallet.
Security experts recommend users to double-check transaction details, verify contract interactions, be wary of “free claim” offers, and use only trusted decentralized applications (dApps) to protect against such attacks.
To enhance wallet security, suggestions include implementing dynamic refresh based on block time, forcing simulation refresh before signing, displaying simulation timestamps, integrating phishing contract blocklists, and alerting for outdated simulation results.
This type of attack represents an advanced evolution in phishing strategies, highlighting the need for vigilance and verification through multiple sources when dealing with blockchain transactions.