Original Author: Biteye Core Contributor Viee
Original Editor: Biteye Core Contributor Crush
Published on: November 20, 2024
Recently, on-chain activity has surged, with mascot-themed coins skyrocketing by 60,000% and the rise of DeSci narratives. Meme coins have become the dark horse of this bull market!
On-chain operations can be complex. In this tutorial, Biteye will guide beginners step-by-step on using GMGN to engage with Meme coins!
A more advanced guide will follow; stay tuned.
This article focuses on new launches, teaching you how to find, analyze, and trade newly listed Meme coins.
1. Discovering New Meme Coins
1.1 Using GMGN’s Discover Feature
GMGN provides a “Discover” feature that allows users to find newly created tokens on various chains:
- Ethereum: https://gmgn.ai/discover?chain=eth
- Solana: https://gmgn.ai/discover/?chain=sol
- Blast: https://gmgn.ai/discover?chain=blast
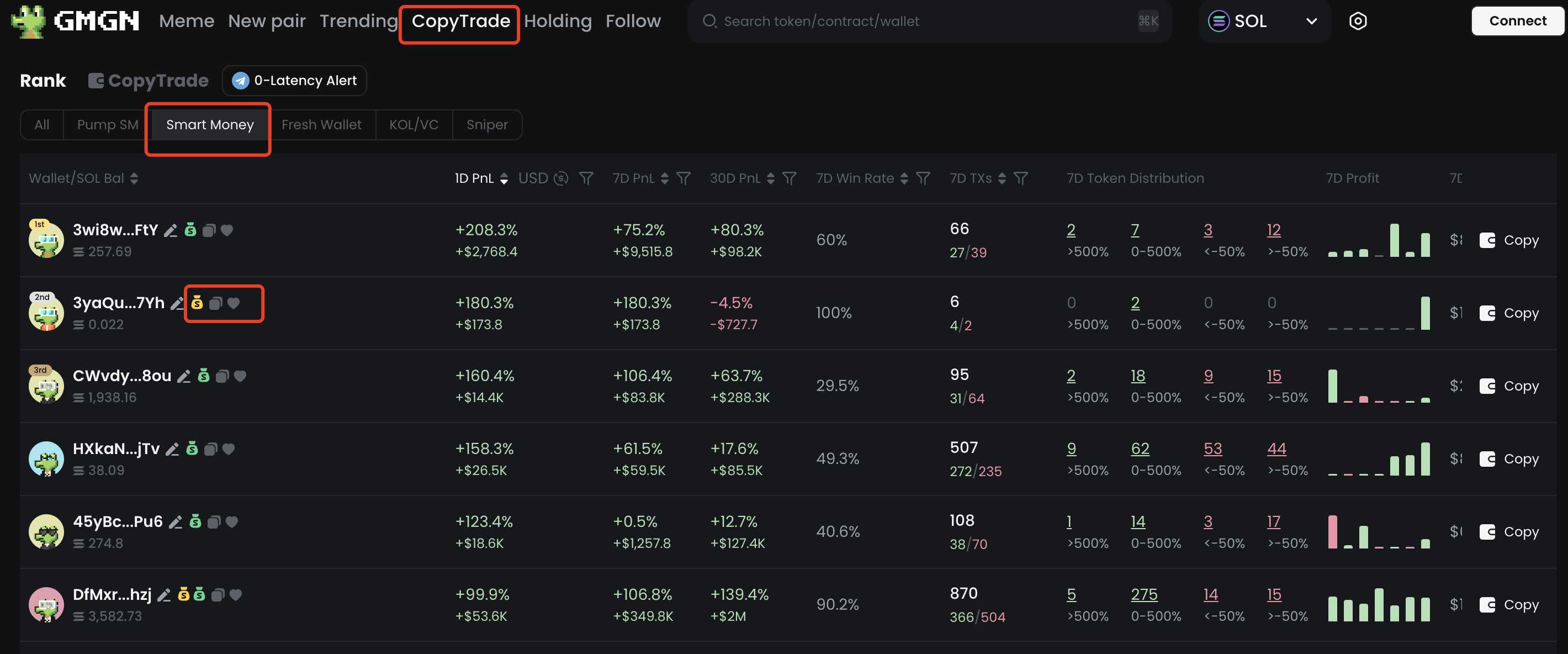
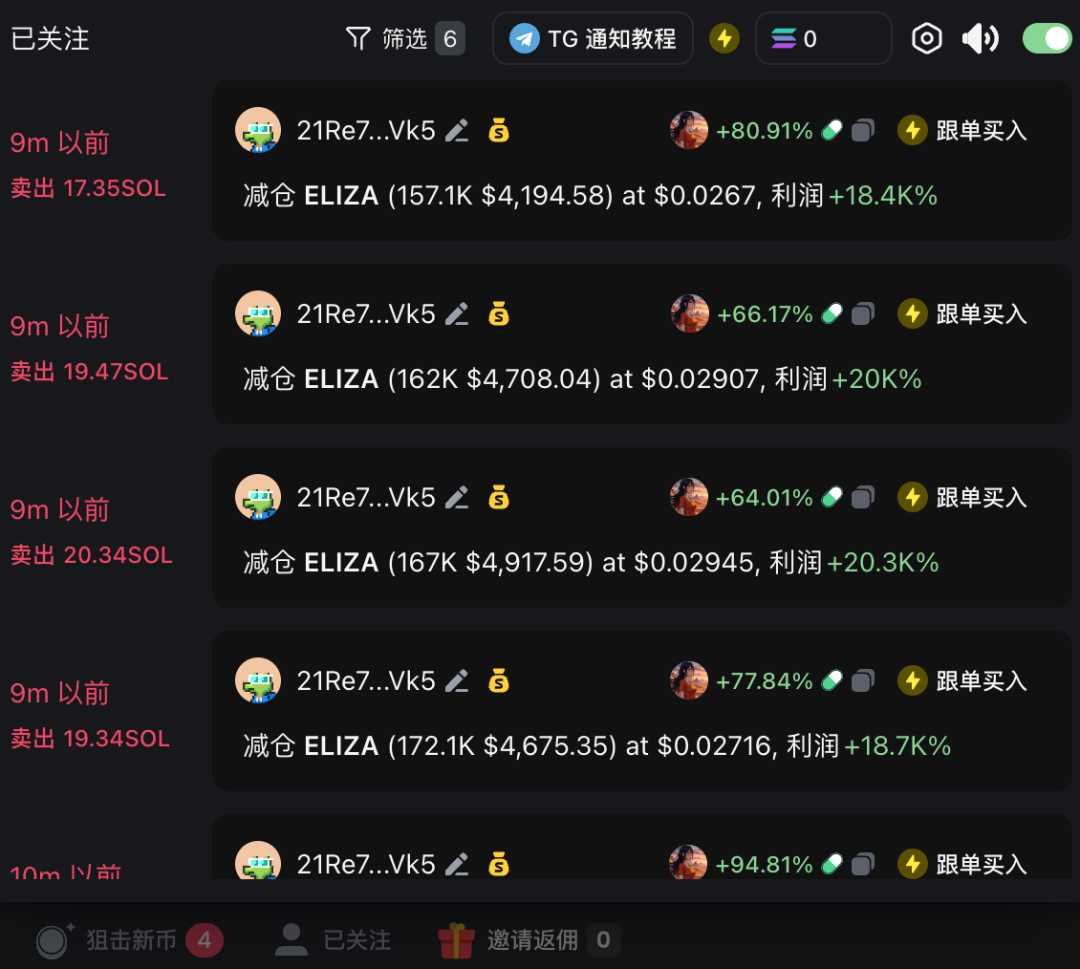
1.2 Following Smart Money
By following wallets labeled as “Smart Money,” you can receive real-time notifications of their activities, including buys, sells, and position changes. GMGN also offers Telegram integration for instant alerts.
When choosing wallets to follow, consider your trading habits to avoid information overload. It’s advisable to track wallets that align with your style to ensure efficient information flow.
Note: Always check contract security, as some smart money may invest without thorough contract verification.
2. Analyzing Meme Coins
2.1 Information Sources
- Twitter Monitoring: Follow various Meme coin-related KOL accounts and join discussion groups to stay updated.
- On-Chain Monitoring: Keep an eye on tokens transitioning from small markets (inner markets) to larger ones (outer markets) and assess their investment potential.
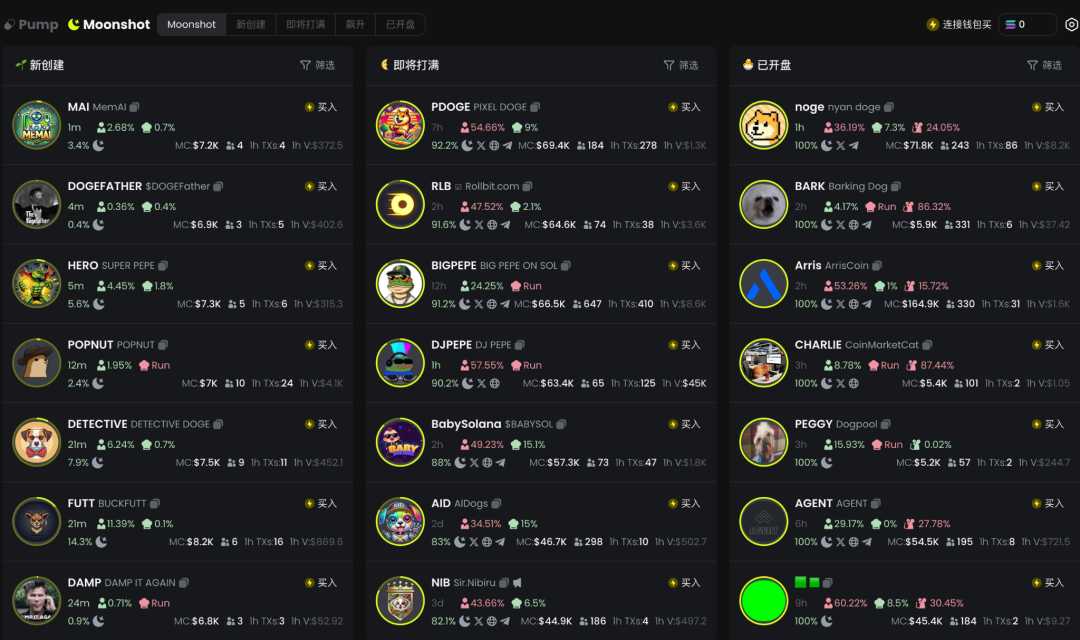
GMGN categorizes tokens into three types:
- Newly created inner market tokens (highest risk)
- Tokens nearing inner market cap limits
- Tokens that have entered outer markets (lower risk)
Inner Market vs. Outer Market:
- Inner Market: Before reaching a market cap of $69,000, tokens are in the inner market, representing an early and high-risk stage.
- Outer Market: After surpassing $69,000 and adding liquidity to platforms like Raydium, tokens enter the outer market, indicating further development and reduced risk.
It’s recommended to focus on tokens that have entered the outer market. While still risky, they are relatively safer for beginners and may offer substantial profit potential.
Caution: Entry into the outer market doesn’t guarantee price appreciation. Many tokens plummet post-listing; always exercise caution!
2.2 Case Studies
- $SLERF: The founder accidentally burned liquidity pool tokens, airdrop reserves, and minted tokens, sparking bullish sentiment and rapid exchange listings.
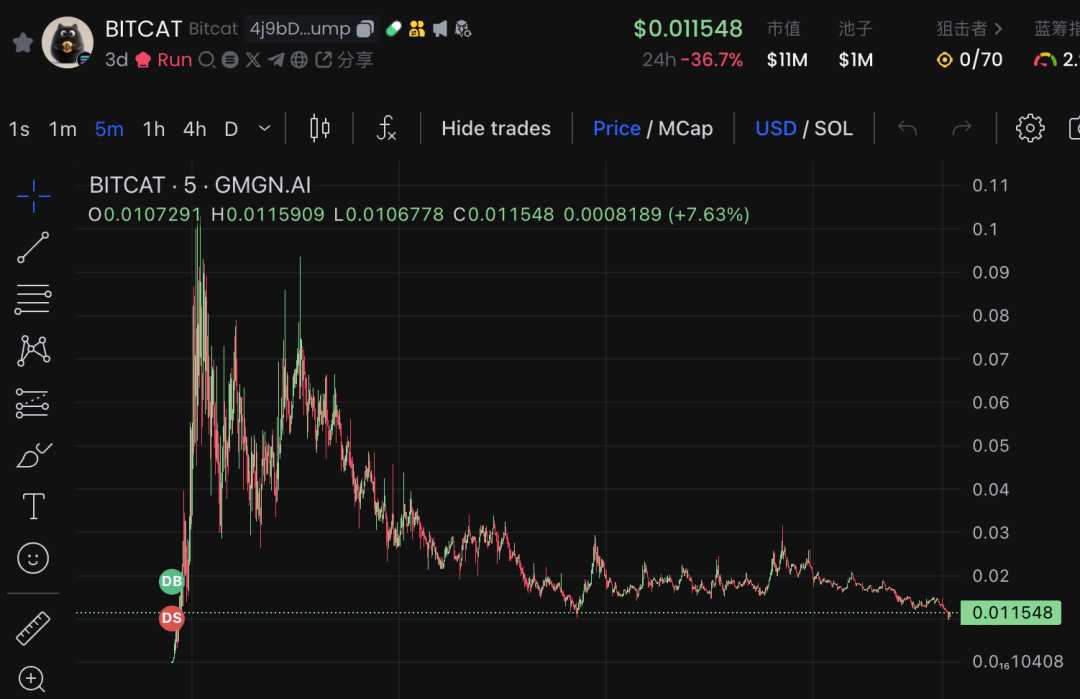
- $BITCAT: Amidst growing interest in “mascot” concepts, Bitcoin’s official Twitter posted a black cat image, leading to speculation about a Bitcoin mascot. The related token, $BITCAT, surged from a market cap of hundreds of thousands to $100 million within three hours, later stabilizing around $50 million.
Recommendations:
- Early Entry: Ideal at market caps of a few hundred thousand. Avoid chasing highs above $10 million to prevent being trapped.
- Post-Drop Entry: If confident in the narrative’s longevity, consider entering after an 80% price drop to mitigate risk.
3. Trading Meme Coins
3.1 Using GMGN’s Trading Interface
GMGN’s trading interface offers several features:
- Contract Verification: Check for potential issues like developer privileges or blacklists.
- Transaction Monitoring: View metrics such as transaction volume, liquidity, minting data, and blacklist status.
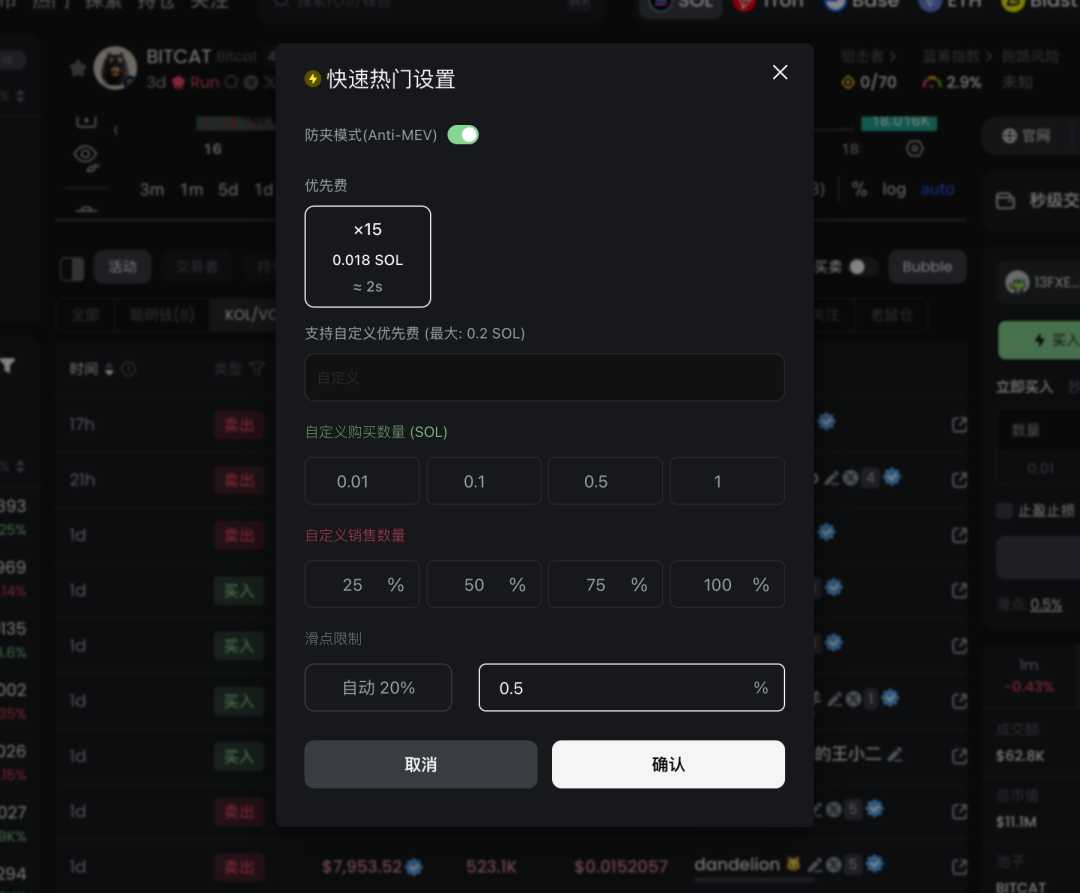
- Anti-MEV Protection: Enable anti-MEV mode to prevent sandwich attacks.
- Slippage Settings: Adjust slippage tolerance to balance transaction speed and price accuracy.
Note: Higher slippage increases transaction speed but may lead to less favorable prices. Typically, a 0.5% slippage is sufficient; during high volatility, consider increasing it to 10%.
4. Risk Disclaimer
Every day, hundreds of Meme coins emerge, with most destined to fail. The chances of finding a “golden dog” (tokens reaching tens or hundreds of millions in market cap) are slim, let alone those listing on major exchanges.
In summary, higher returns come with higher risks. Please take responsibility for your investments!